ESP - Role based access control
ROLE-BASED ACCESS CONTROL FOR SYSTEMS AND USERS
Protecting critical resources from unauthorized systems and users represents one of the most important cyber security concerns for enterprises today. The “unauthorized” threat is not limited solely to a user who lacks the appropriate privileges. It can also refer to a machine from which the user is accessing a resource that is: unapproved for the type of access requested, unknown to the organization, or fails to meet required security standards as defined in the organization's security policies.
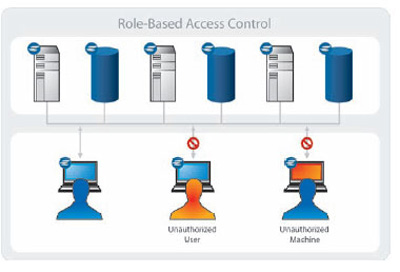
This challenge has been made greater by factors such as an increasingly mobile workforce, dependence on contractors and guest workers, and unapproved usage of personal machines. Similarly, the portability of users' access credentials exacerbates the situation. As a result, organizations need to have the ability to ensure that any machine from which a user attempts access is subject to and compliant with appropriate security policies. Enterprise IT organizations commonly look to identity and access management (IAM) solutions to provide a framework to restrict a user's right to access systems and applications, but these solutions often fail to account for the current security posture of the machine from which the access is being initiated.
Effectively remedying this situation requires a unified policy-based approach that manages access based on the roles of individual machines and users, and provides the ability to both authorize and verify the security posture of requesting machines before access is granted.
Employ the Principal of Least Privilege for efficient role-based access control!
With Elemental you can protect against the misuse of stolen credentials, privilege escalation and lateral movement of malware by applying the principal of least privilege as a prerequisite to efficient Role-Based Access Control.
Many best-practices and regulatory compliance frameworks (CIS, HITRUST, NIST, HIPAA, SOX, etc.) mandate the application of this principle to access any digital asset.
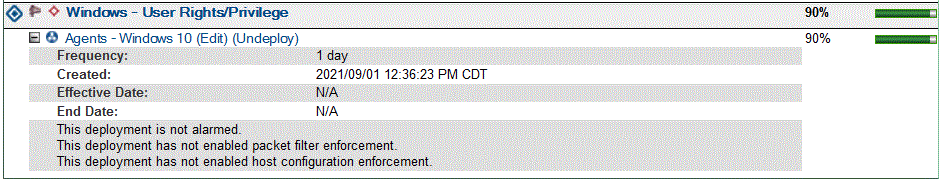
Defining, applying and enforcing security policies that check proper user rights on every machine is best practice to control privilege abuse.
The Elemental Security Platform (ESP) provides the industry's only comprehensive solution for the continuous protection of critical network resources. It combines automated device discovery, targeting of policies (to both users and machines), continuous compliance monitoring, and adaptive host-level access controls - all within a single policy-based application. This integrated approach to managing communications - both within the network as well as across the perimeter - ensures that machines granted access to an organization's key computing assets not only are fully authorized, but also are in compliance with their assigned security policies.
How it's done with ESP? -> Learn more >>>