SOC 2 Compliance with ESP
System and Organization Control 2 - SOC 2 Comliance with ESP
* Is your company spending too much time implementing technical security controls needed for the System and Organization Control 2 (SOC 2) report?
* Are you lacking the tools needed to continuously manage, monitor, and enforce your SOC 2 security configuration and policies?
* Do you wish you had a continuous and consistent reporting mechanism to provide historical compliance evidence to auditors and management?
Elemental is here to help!
Elemental Security Platform (ESP) is one of the most advanced cybersecurity, compliance, and risk management automation platforms on the market. Lightweight, intelligent, and scalable for any network, from small businesses to large enterprises, it offers easy out-of-the-box deployment, continuous and automated management, and auditor-proof enforcement of technical controls needed for the Security trust principles of SOC 2. Hundred of controls in the form of actionable (automatically and continuously executable by a program) security policies can be deployed to your servers and other hosts in a matter of minutes, providing instant feedback on compliance and risk levels in your environment. Afterward, those controls are monitored and enforced 24/7, with precise reporting on policy outcomes available to your team with a click of a button.
SECURITY Controls are the Common Criteria for the Trust Services Criteria
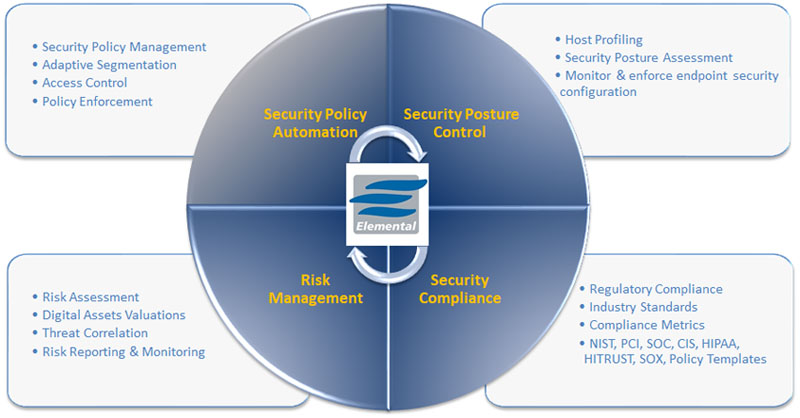
SOC 2 Security - Trust Services Criteria (TSC) controls at your fingertips
- - Pre-mapped, executable SOC 2 security policies ready to be deployed to your servers, desktops, laptops
- - Easy-to-understand compliance and risk scorecards for all endpoints
- - Access controls and micro-segmentation
- - Host security configuration management
- - Built-in inventory of hosts, configurations, software, hardware
- - Control of host activities
System of Records
- - Records of all SOC 2 policies and controls deployed via ESP across the entire network
- - Historical records of hosts' compliance and risk postures
- - Time-stamped records of policy execution and enforcement actions
- - Detailed documentation of all policy exceptions
- - Ability to demonstrate continuous compliance
Unified Control Management
- - Ability to incorporate and manage controls for multiple frameworks simultaneously (PCI DSS, HIPAA/HITRUST, SOX, NIST 800, and more)
- - Out of the box drag-and-drop functionality, no coding or scripting needed to design or execute policies
- - Consistency of policy deployments across different networks, operating systems, premise or cloud environments, geographical locations
- - Instant discovery of missing or misconfigured controls (discovery of compliance gaps)
Risk and value assessment of digital assets
- - Customizable and consistent risk and value parameters for all endpoints
- - Near-real-time risk scorecards reflecting current host activities and configurations
- - Historical tracking of risk levels across the entire network or for individual host groups
Go beyond compliance
- - Drastically increase security through micro-segmentation
- - Harden your network to make it more resistant to common security attacks
- - Implement defense-in-depth strategies
- - Use automation to detect and mitigate suspicious host behaviors