Risk, Security, Compliance Control - Elemental Technology
Elemental Security Platform is the most integrated and capable Automation Solution for Cyber Security Assurance, Compliance Assessment and Risk Management.

Risk - Security - Compliance beyond GRC!
A solution that aligns security operations with business objectives.
By continually responding to the latest threat or regulatory requirement with another new tool, the cyber security industry has contributed to the fragmentation of the offer and the persistence of manual processes that make computer security problems virtually unmanageable. The problem that organizations are constantly facing is a permanent disconnect — the implementation gap — between the defined, written security policies and the actual status of any IT infrastructure.
Elemental Security Platform (ESP) is the only solution that unifies the key features needed for enterprises to translate their broadly defined cyber security objectives into specific security policies (controls) that can be automatically deployed, monitored, adjusted, enforced and reported on for all endpoint systems in the network.
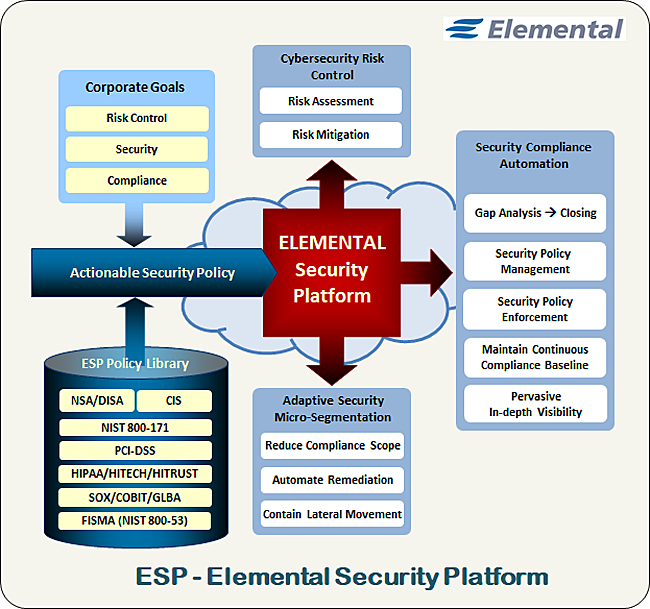
ESP extends your GRC (Governance Risk and Compliance/Control) solution by mapping individual mandates from industry standards or regulatory compliance frameworks to actionable technical IT security controls that can be implemented on any of your most startegic endpoints in any location or environment.
The Elemental solution provides a fully automated enterprise software platform that unifies the key technologies required to effectively manage cyber security policy lifecycle, compliance, system configuration and mitigate IT risk. This comprehensive approach enables organizations to realize their internal cyber security and compliance goals by combining:
- An extensive library of security controls and policy templates
- Tightly integrated technical security controls governing system configuration, utilization and network access
- Automated implementation, monitoring, and enforcement of security policies
- Policy self-adaptation to system and network security posture changes
- Auto-discovery of unauthorized or unmanaged devices
- Continuous monitoring of system integrity and compliance
- Measuring and reporting of security posture, compliance, risk, and value of digital assets

Automate Security Policy Compliance
ESP provides deep visibility into the state and activity of each endpoint on the network. This enables a high degree of automation that quickly identifies changes on individual systems and automatically updates their policies. An unparalleled level of automation is delivered through unique features — including dynamic grouping, self updating policy deployments, and risk assessment capabilities — that provide a clear and continuous understanding of the individual roles of systems, applications and users, as well as the observed characteristics, security posture, associated risk and value of individual endpoints.
The unprecedented level of security intelligence and policy-based controls delivered by the Elemental platform is not limited to systems running the ESP agent. Passive discovery, monitoring, and classification of unmanaged endpoints also allow administrators to readily expose rogue devices and apply policies throughout the network to restrict their access to key systems.
Close the Policy Implementation Gap
The security industry has responded to this dilemma by introducing a dizzying array of products designed to link business-based IT objectives with measurable results. However, these offerings have all targeted very narrow aspects of this enormous challenge. This siloed approach has driven administrators to attempt to manage security policies through organizational integrations and costly and resource-intensive manual workarounds. The result is a policy implementation gap that leaves most organizations exposed to significant risks.
What if they could somehow achieve full knowledge regarding the state and activity of all these elements?
Keeping track of the myriad changes, and manually checking and rechecking that the right security policies are on the right systems at the right time can introduce errors and is prohibitively time and resource intensive.
Monitor and Control Endpoint Security Posture - it determines your Attack Surface
Elemental Agents continuously collect data about the endpoints they are running on which enables the ESP system to automatically profile and place them in policy target host groups. This constant gathering of hosts attributes enables a real-time assessment of a system's security posture and by deploying and enforcing specific hardening controls it also allows for a reduction of those systems' attack surface.
- - Auto-Discovery – the Elemental agents passively monitor the network for new computers. Unauthorized machines are quickly discovered and classified to identify their operating system, hardware details, and networking activity.
- - Security Configuration – get an in-depth profile of the operating system, network properties, application settings, and system config-uration parameters.
- - Users and Accounts – accounts and user logon activity are tracked by ESP enabling implementation of policies based on user roles and entitlements.
- - Hardware and Software Inventory – the Elemental agent gathers a detailed summary of devices, installed applica-tions, running processes and services.
- - Network Communications – detailed traffic information for both managed and unmanaged computers enables administrators to mon-itor and regulate traffic for systems, applications, users, and network segments.
Monitor Compliance and Enforce Policies
Security executives have too much data and not enough information from disparate sources, such as asset and inventory products, configuration and event management systems, network and host-based security scanners, log analyzers, and the like. They hope to weave all this data together to serve as a foundation for managing their security policy. However, this fragmented and manual process is expensive, resource and labor-intensive, and error-prone. The solution involves automating the acquisition and correlation of this mountain of data to help guide the management of appropriate security policies while enforceing controls whenever necessary.
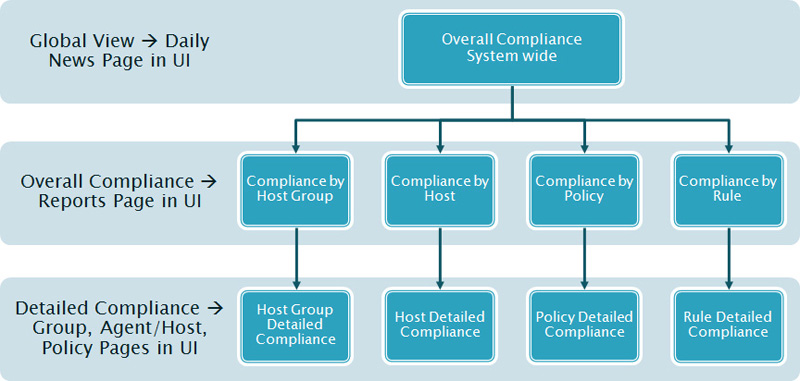
Provide Metrics and Reporting
The Elemental system provides extensive reporting capabilities, including a suite of executive dashboards, detailed views and histories of compliance, risk and value, network traffic activity, and trouble ticket administration. The ESP reporting makes it easy for administrators to document the state of their networked systems and to identify changes that occur on individual systems or in the communications between systems.
High-level business-aligned reporting combined with drill-downs into the detailed technical information serves the needs of Chief Security Officers to report on the status of the organization's overall security and compliance efforts. At the same time, it enables IT security managers to address specific issues that may affect these metrics.

Maintain and Enhance Security and Regulatory Compliance
Elemental provides the framework to achieve compliance with industry and government regulations, this includes an extensive policy templates library.
ESP ships with several thousand individual technical controls (rules), plus an extensive array of pre-defined, editable security policy templates for:
- • OS and application security baselines: NSA, CIS, NIST, DISA (STIG), and Microsoft
- • Regulatory requirements: HITRUST, NIST 800-171, SOX, PCI-DSS, HIPAA/HITECH, FISMA (NIST 800-53), GLBA, etc.
- • Security zones—micro segmentation: access controls to regulate network traffic among users, systems, workloads, groups, etc.
- • Security configuration management and activity controls
Monitor and Enforce NIST 800-171 Compliance
Protecting controlled unclassifed data in nonfederal information systems and organizations is achievable using Elemental's predefined policy templates library and automated policy deployment, monitoring and enforcement capabilities. Most computing infrastuctures are highly dynamic, so one cannot rely on periodic snapshots to safeguard covered information. Therefore, one must also monitor and enforce security controls on an ongoing basis to ensure their continued effectiveness. When the inevitable issues are discovered, they must be communicated upon internally and corrective actions must be implemented. This is where the ESP solution provides peace-of-mind to be confident about being cyber secure while also NIST (National Institute of Standards and Technology) SP800-171 compliant.
Comply with the Sarbanes-Oxley Act (SOX)
The Sarbanes-Oxley Act (SOX) requires that CEOs stand behind the IT controls involved in financial reporting. Elemental helps enterprises meet this standard by making it easier to document their controls and prove to auditors that each has been properly implemented, maintained and monitored.
Implement the HITRUST Common Security Framework
The HITRUST Common Security Framework (CSF) is becoming one of the most popular security and compliance standards in the healthcare industry due to the standardization of controls needed to “demonstrate” compliance. But the prescriptive nature of HITRUST puts a spotlight on the “nuts and bolts” aspects of cyber security – the endpoint level technical controls. Elemental not only insures compliance with HITRUST/CSF is rapidely and effortlessly met, but is also continuously maintained and enhanced.

Comply with the Comprehensive Health Insurance Portability and Accountability Act (HIPAA)
Elemental provides a framework for deploying and enforcing policies on computing resources that store and have access to patient health care information. This comprehensive solution makes it easy for a broad range of organizations - from banks to universities to healthcare providers - to adhere to HIPAA best practices for network access control, host security configuration management, as well as systems and software inventory controls.
Meet the Payment Card Industry (PCI) Data Security Standards
Elemental enables enterprises to adhere to PCI best practice security standards for building and maintaining secure networks, controlling access to cardholder data, and implementing a policy-based approach to monitoring and securing enterprise networks. The Elemental solution delivers the visibility, control, and automation necessary to protect cardholder information as well as the systems that host the applications through which it is processed and delivered.

Protect Corporate Digital Assets
Layered Protection – As a value-add compliment to infrastructure level network admission control solutions ESP provides highly targeted, granular, and always-on host level access controls that ensures only secure and authorized machines are granted access to critical systems.
Control Access with Adaptive Micro-Segmentation
Stop cyber threats by controlling the lateral movement of unauthorized communications across your computing environment. Elemental delivers a unique approach to managing communications that specifically focuses on providing policy-based access control to critical resources. The Elemental Security Platform (ESP) is a solution that empowers organizations to deploy an access control framework that provides a highly granular micro-segmentation of the network that keeps potentially malicious activity in control.
Identify and Contain Unauthorized Systems
Integrated host-level access controls ensure access is denied, whether these unauthorized systems are unknown machines discovered on the network, or known machines that have fallen out of compliance with required polices.
Implement Role Based Access Control
Protecting critical resources from unauthorized systems and users represents one of the most important concerns for enterprises today. Elemental helps to ensure that any machine from which a user attempts access is subject to, and compliant with, appropriate security policies.

Reduce Cyber Risk Exposure while providing deep Insight and Evidence
As IT security organizations struggle to gain a meaningful understanding of the level and sources of risk within their information systems environment, they face a significant challenge in trying to interpret and correlate information generated by all the disparate controls deployed throughout the environment. A _quantitative risk management _approach can provide an important set of business-aligned security metrics to help administrators manage security and compliance initiatives in a way that effectively leverages available resources and protects the key interests of the organization.
Assess Cyber Risk
ESP programmatically determines the value and risk of machines based on a myriad of observed characteristics, roles, behavior, and usage information. The ESP quantifies the value and risk of all machines on the network, both managed and unmanaged, through the analysis of factors including compliance, trust, system properties, the type and volume of networking activity, stored information, and the roles of machines and users. This capability identifies high value and at-risk systems enabling organizations to identify, mitigate, and manage IT risks.
Who - What - When? with Audit Trails
Managing the Who, What, and When of Security Policies and Groups transactions is important evidence for internal and external stakeholders involved in the security compliance process. Audit trails should be transitioned from manual to automated electronic logs that make historical compliance information more accurate, readily accessible, and usable. Successful audit trails demand a top down commitment by upper management, affected departments, and IT personnel. The more quickly an abnormal change or addition is “red-flagged,” the better the response to mitigate against negative influences such as cyber-threats, security breaches, data corruption, or misuse of information.
Monitor and Demonstrate Compliance Trends with Historical Metrics
The Elemental Security Platform helps save both time and money by reducing the frequency of internal audits, by decreasing the effort of measuring and demonstrating compliance with internal and external audit and regulatory requirements. It provides detailed reporting that supports a comprehensive policy framework to ensure system security, manage the configuration of all computers on the network, and monitor compliance.

How is Elemental different?
Elemental's unique Cyber Security Platform enables continuous compliance by actually implementing and enforcing the technical security controls mandated by industry standards and regulatory compliance frameworks. The solution offers faster time-to-compliance, audit-ready reports, improved network security, ready to deploy security policies and risk assessment — all from one unified easy-to-use web based user interface.
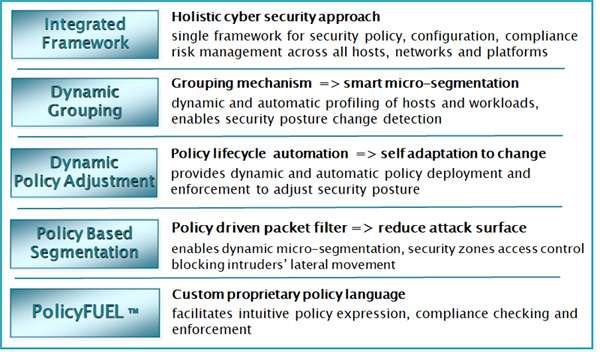
Proven enterprise-class capabilities:
- • Pre-defined out-of-the-box security and regulatory compliance policy templates ready to be customized and deployed
- • Extensive library containing thousands of “drag-and-drop“ cyber security controls (PCI, HIPAA, NIST, SOX, NSA, CIS, industry best practices, etc.)
- • Immediate availability of compliance scores
- • 24/7 monitoring and enforcement of deployed policies
- • Audit-ready logs of all security policies and system use
- • Automation of security configuration management
- • Deep network visibility at any managed endpoint level
- • Real-time and historical compliance and risk metrics
- • Cross-platform containment in case of compromise
Centralized Control with the ESP Management Console
The Elemental Management Console represents a web based graphical user interface (GUI) and is the central control point for security policy management, dynamic policy target group definition, compliance and risk monitoring, as well as reporting. Policy deployments are precisely targeted, automatically deployed, and continuously updated. The ESP enables administrators to import groups from directory services or to specify groups of computers based on their common characteristics, networking behavior, security and risk posture, or user activity.
Align Enterprise Cyber Security with Business Objectives
ESP is a holistic, affordable solution leveraging next-generation technologies to provide tremendous value to security professionals:
- • Improves the efficiency of security and IT staff
- • Unifies visibility across IT security controls
- • Supports the shift from end–point and disparate tools to a holistic and adaptive integrated solution
- • Reduces network attack surface through ‘always-on’ adaptive network access control and micro-segmentation
- • Provides automatic security posture assessment and adjustment
- • Provides business aligned metrics to measure the compliance, value, and risk of systems
- • Reduces time and cost for audits

Click here to request more information or an online demo
