ESP Policy Gap
The Security Policy Implementation Gap
You can't secure what you don't know!
Whether it’s ensuring business continuity, better defending their critical assets, or becoming SOX, PCI or HIPAA compliant, security professionals readily understand these business-based IT goals. Their challenge lies in translating these broadly defined objectives into actual security states on the thousands of elements that comprise their networks.
The constantly changing environment of today’s enterprise networks compounds the problem. At any given time, administrators find it hard to know the true state of the countless individual machines and systems that are connected to their networks—and they can’t manage what they don’t know.
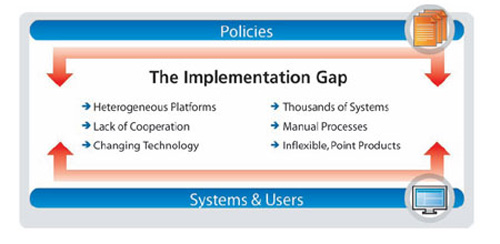
Closing the Security Policy Gap
Elemental has developed the first functionally integrated solution that lets security administrators meet their broad-based security objectives in dynamic, real-world enterprise environments. It provides an unprecedented view into the network, including an up-to-the-moment security posture of every machine. Using this highly detailed view, Elemental's solution enables security professionals to achieve their business goals by quickly translating high-level security policies into the desired security states on each and every affected machine on the network.
It allows security professionals to measure, monitor, and enforce their desired security states, while also providing full reporting capabilities. As a result, enterprises can for the first time obtain meaningful metrics, measurably improve their security, and satisfy compliance requirements using a single product:
the Elemental Security Platform (ESP).
Elemental reduces security threats and risks of non-compliance by making it easier to translate business objectives into well-developed policies and express these across the network. A well-developed security policy is rooted in best practices and:
- - Takes into account business/organizational goals as well as the technical environment
- - It allows for exceptions and is flexible enough to reflect business realities
- - Provides a consistent set of metrics that support continued improvement in security process and practices
- - Supports hierarchical expression of policies, i.e. enables a high-level overview supported by a detailed drill-down
- - Is consistently implemented across computing platforms and organizational boundaries