Containing Unauthorized Systems
ESP contains unauthorized systems
The Challenge
A key problem facing network and security administrators is the threat posed by the introduction of unauthorized computers into their networks. These hosts can carry worms and viruses not mitigated by security countermeasures and can leave critical networked assets vulnerable to intrusion or attack.
A fundamental evolution in the dynamic way networks are used has resulted in nearly all enterprise computing assets being connected within very few degrees of separation to public wide area networks. The proliferation of wireless-capable networking devices only compounds this problem. As a result, the distributed perimeter, combined with the continuing challenge of keeping employees and guests from bringing unauthorized devices onto the network, have made it a top security priority to identify rogue machines and to protect business-critical computing assets.
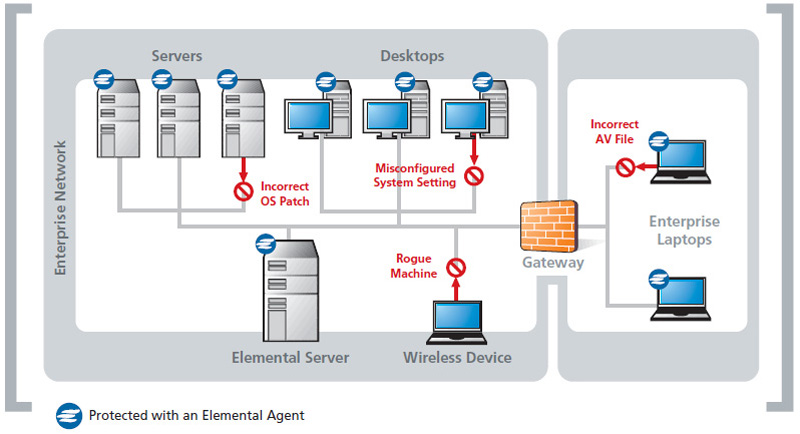
The Elemental Security Platform provides a unique approach to identify and contain unauthorized machines. Using passive detection processes and adaptive host-level access controls, the Elemental system empowers security managers to use a policy-based approach to secure network communications and to contain or quarantine machines that are either unknown or non-compliant with the organization’s computer security policies.
Discovering and Profiling New Hosts
The Elemental Security Platform is an agent-server security software system that provides a comprehensive policy-based solution for managing host-level security. In addition to configuration management policies, the Elemental agent also provides a policy-based packet filter. This capability supports the implementation of multi-layer security policies that not only govern the security of the host and its resident applications, but can grant or deny access to other hosts on the network. These unified multi-layer policies enable an unprecedented holistic approach to managing host security.
In addition, the Elemental agent provides a passive listening capability to identify new hosts that appear on the network. By monitoring all broadcast traffic, and by monitoring network connections involving machines not running the agent, new computers on the network are quickly discovered. Additionally, the Elemental agents perform numerous discovery operations such as passive fingerprinting and signature matching on networking activity to profile the configuration and networked application activity of new hosts. With agents deployed over the network, the Elemental system essentially provides a distributed “passive sonar” net that rapidly sees every host connecting to the network.
All Elemental agents are assigned a unique identifier, eliminating the traditional complexity of managing security using identities based on IP addresses in dynamic computing environments. The IP address of a managed host at any given time is known, as well as all the IPs that host has used on any of its network interfaces over time. New machines not running the agent are identified by a previously unseen MAC and IP address pairing being detected by an agent. All discovery activity is reported to the Elemental server, which then updates the agent population about the presence and security posture of discovered hosts.
The continuous nature of the Elemental solution enables host-level access controls that adapt to changes on the network.