ESP Security Posture
Security Posture Assessment provides Situational Awareness
While security professionals understand the business goals and realities that define the right policies, in a changing environment they find it hard to know the true state of the network. More than half the elements in a typical network are changing every year, people are revolving in and out of the organization at a rapid rate, and rogue machines, outsourcing, and consultants constantly inject unknown risks.

Poorly configured systems weaken your security posture
Findings in Verizon’s recent 2020 Data Breach Investigations Report show that “misconfiguration” is among the top five action varieties in breaches.
This suggests that poorly configured systems lead to more breaches than exploited systems, more than malware like ransomware or trojans, but most organizations don’t put the same resources on finding and fixing misconfigurations as they do in vulnerability scanning – we would have to deal with a lot less vulnerabilities to begin with if most of our systems were properly configured to minimize exposure to data breach. Understandably so, because running a vulnerability scanner once in while is easy, but assessing misconfigurations (and fixing them) is usually a tedious and often expert undertaking.
Consider the Elemental Security Platform - ESP software to efficiently as well as economically assess and enhance your security posture by:
- Automatically securing configurations so they never change due to bad actors or fat fingered employees.
- Notifying you when changes occur.
- Enforcing security policies across computing infrastructure, so if something were to happen it will promptly be changed back.
- Allowing you to easily incorporate industry security standards such as NIST, HIPAA, HITRUST, PCI-DSS, SOX, CIS, and many more into your own policies.
ESP does this through a combination of technologies producing an efficient and economical way to deploy, monitor and enforce security policies containing hundreds of actionable security controls (rules) that automatically check and fix misconfigured systems and enhance their respective security posture against potential vulnerabilities and corresponding exploits.
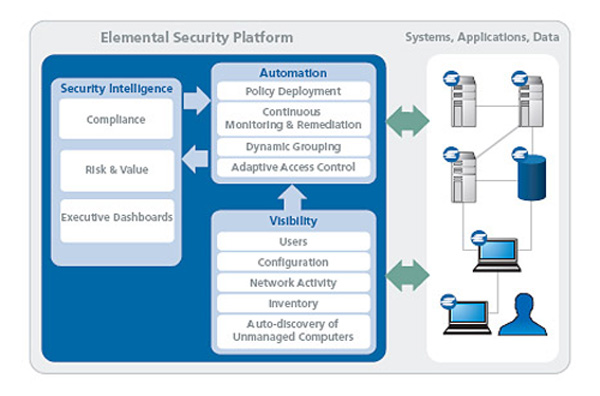
Comprehensive Visibility with Context
ESP provides deep visibility and context for continuous security posture assessment.
Elemental is making every endpoint system, physical or virtual, on-premise or in the cloud, anywhere on the network transparent to security administrators.
The transparency provided by the Elemental solution covers all major operational aspects of computers while exposing misconfigurations which become security vulnerabilities.
ESP is the first and only solution that concurrently monitors a machine's inventory, configuration, and network traffic-all under a single unified policy management framework.
Some of the key information determined about an endpoint system on the network includes:
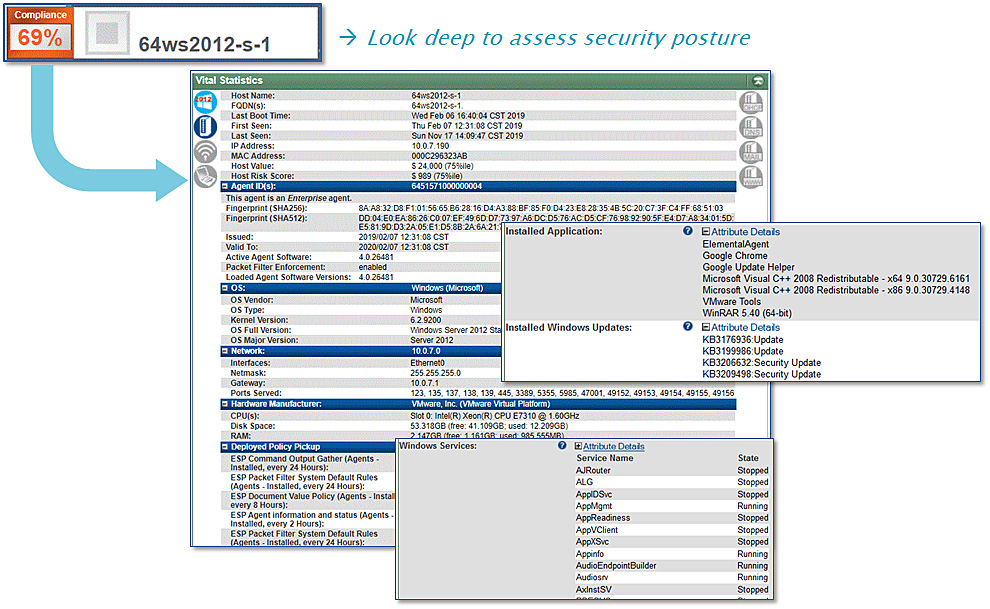
Inventory – The Elemental Security Platform continuously monitors each machine's installed software and hardware inventory. It quickly discovers changes, such as the installation or launch of a new application or device. This allows security administrators to readily spot anomalous activity and to implement policies to restrict the operation of machines to their intended business purpose.
Host Configuration – ESP can identify a wide variety of configuration settings for a machine's operating system, including its applications, remote connectivity, processes and services, account and file permissions, file system content, and system performance.
Policies and Compliance – A key aspect of base-lining and monitoring the state of machines involves determining their current compliance posture vis-à-vis industry accepted policies. These policies not only include standard best practices as designed by the CIS (Center for Internet Security) and NSA (National Security Agency), but also templates to address regulatory compliance requirements such as SOX, HIPAA, NIST or PCI.
Users – The Elemental solution makes it possible to have visibility into who is logged in and what users are doing across the network. This enables policies to be implemented in a manner that addresses the rights and responsibilities of different parts of the organization.
Network Traffic – The ESP agent continuously monitors traffic coming in and out of its host computer to identify machines, systems, and applications that are communicating on the network. The agent also passively listens to network traffic to expose, classify, and track unmanaged or unapproved machines.
This awareness of network elements and activity enables administrators to:
- > Automatically configure machines in accordance with regulatory requirements and security best practices
- > Assure that only approved hardware and software have access to key systems
- > Discover and contain new machines coming on the network
- > Restrict the ability of unauthorized or non-compliant machines to harm critical resources
ESP goes beyond system hardening by centrally controlling security trust zones.
ESP's enforceable traffic flow policies block lateral movement and facilitate a zero trust network architecture.