Role Based Access Control
ESP Case study: Role Based Access Control
The Problem
Protecting critical resources from unauthorized systems and users represents one of the most important cyber security concerns for enterprises today. The “unauthorized” threat is not limited solely to a user who lacks the appropriate privileges. It can also refer to a machine instance from which the user is accessing a resource that is: unapproved for the type of access requested, unknown to the organization, or fails to meet required security standards as defined in the organization's security policies.
Effectively remedying this situation requires a unified policy-based approach that manages access based on the roles of individual machines and users, and provides the ability to both authorize and verify the security posture of requesting machines before access is granted.
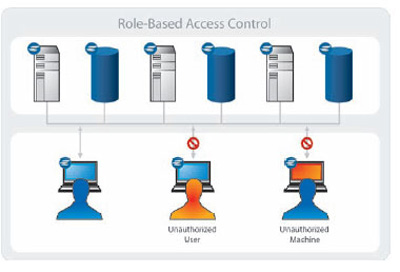
The Solution
The Elemental Security Platform (ESP) provides the industry's only comprehensive solution for the continuous protection of critical network resources. It combines automated device discovery, targeting of policies (to both users and machines), continuous compliance monitoring, and adaptive host-level access controls - all within a single policy-based application. This integrated approach to managing communications - both within the network as well as across the perimeter - ensures that machines granted access to an organization's key computing assets not only are fully authorized, but also are in compliance with their assigned security policies.
ESP makes it easy:
‘Out-of-the-box’ ESP provides you with thousands of powerful technical controls called the Elemental Rules. You select these rules from the ESP Policy Library to express your own User Rights Policy. With a few click you can organize these rules in a policy while customizing each of them following your own requirements, or you can just use the default values in one of our policy templates.
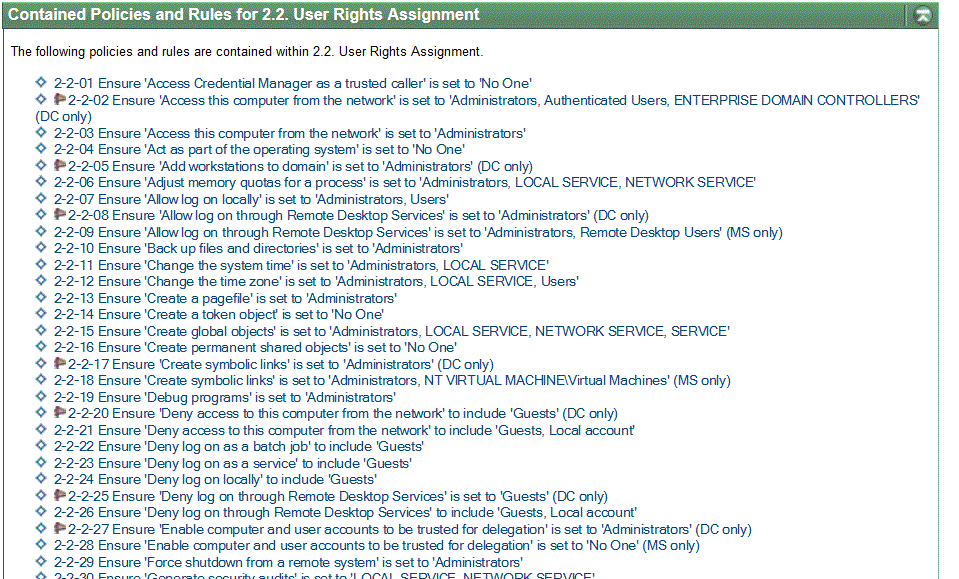
In Windows environments for example, ESP provides you with the automation necessary to maintain a consistent set of more than 40 customizable Windows user/group rights policies for any type of server or client machine throughout your organization.
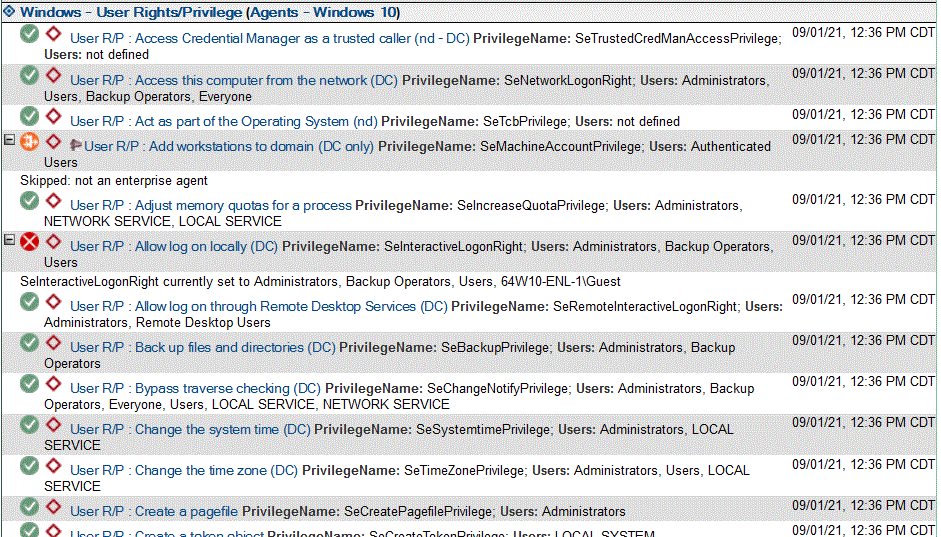
Once the User Rights Policy created, you can deploy it to a predefined or user defined group of target hosts and let it do the work of compliance assessment or enforcement for you.
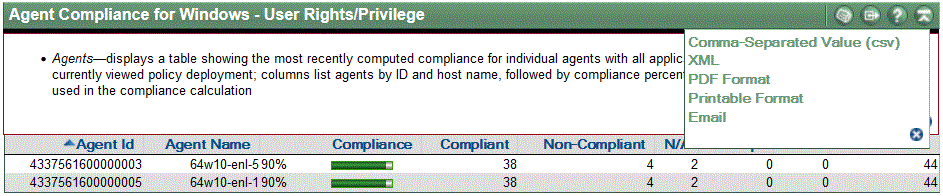
ESP system automatically groups the non-compliant hosts in a dedicated group to which a containment policy using specific blocking rules is applied. This implements access control to and from these hosts which are in violation of the principal of least privilege.
The containment policy actively isolates non-compliant hosts as long as there are members in the corresponding group this policy is targeting.
If you want to automatically enforce those user rights, you can do it by deploying the User Rights Policies in enforcement mode. You should keep the containment policy active just in case any unexpected/unauthorized changes might take place.
With ESP capable policy engine, real-time and historical reporting, you can easily and economically demonstrate and continuously maintain compliance with the Principal of Least Privilege !

Knowing Who and What Are On the Network
The Elemental solution provides an unparalleled level of visibility into the network environment. The ESP agent, which runs on server and desktop operating systems in the cloud or on-premise, continuously monitors the configuration, inventory, policy compliance, user logon, and network activity of its host machine. Additionally, each agent constantly surveys the network for the presence of unmanaged machines. Upon detection, it passively classifies unmanaged machines based on their observed host properties and networking activity.
This in-depth visibility creates a clear understanding of roles in the network environment - the who, what, where, and when. These roles can be based on the identity and access rights of users (ESP can natively use directory services such as Active Directory), the security posture and profile of computers (such as what applications are running or installed, or their patch levels), the physical or virtual location of hosts (sub-nets, time zones, and more), as well as alignment with business schedules. In addition, the continued compliance with assigned policies is a key criterion that can be used to define the roles of machines on the network (such as whether they're running up-to-date anti-virus software or are compliant with your full suite of SOX policies).
Protecting Critical Resources
The in-depth view and role-based context provided by ESP enables policies to be accurately targeted to individual users and machines based on defined roles and business objectives. Access control policies implemented at the host level ensure that only users with appropriate privileges are granted access and that machines from which they are requesting access are both authorized and compliant with their assigned policies.
The ESP solution monitors all network traffic going in and out of managed machines and controls access based on an organization's security policies. Policies are centrally managed and locally implemented on each managed machine instance. When violations are detected, responses can range from simply reporting these violations-raising awareness of unauthorized activity to automatically enforcing policies that deny unauthorized network activity.
Adapting To Change
The detailed visibility of users and machines provided by the Elemental system provides an automated policy management infrastructure that enables enterprises to easily administer policies for all communications on their networks. Policies are applied to groups of hosts or users and automatically updated as changes in the state of machines or the activity of users is detected. IT staff can simply specify policies controlling access for groups of hosts or users that have the right to communicate, and whether either has the right to access protected resources.
This continuous and detailed view into the network landscape enables the Elemental solution to quickly identify and control access to any machine observed on the network. For managed machines running the ESP agent, this may mean automatically restricting the ability to connect to key servers if they fall out of compliance with their respective policies. For unmanaged machines, it can enable IT staff to implement granular access controls, such as allowing guests to have access to a limited set of applications or data while still ensuring they can't access key resources.
A Comprehensive and Layered Defense
Traditional security methods seek to control network access at gateway devices and infrastructure (routers, switches, firewalls, etc.), application, and data servers, but fail to protect network resources once the first lines of defense have been breached. The Elemental system bridges this security gap by unifying the processes of managing access control for systems and users, and by ensuring that authorized communications take place only between machines that can demonstrate up-to-the-moment compliance with their assigned security policies.
Click here to request more information or an online demo
