
by: Elena Garrett
Elemental Micro-Segmentation vs. Traditional Network Segmentation
What is network micro-segmentation? How is it different from what most companies do now? How does micro-segmentation affect network security? Let's explore!
Micro-segmentation in cyber security
Most companies today use network-dependent segmentation. A traditional approach to network security was built around a strong network perimeter defense and utilized concepts like subnets, ports, protocols, and virtual LANs (VLANs) to differentiate between traffic from different parts of the network. Various software and hardware security products were placed around the perimeter to detect and handle suspicious or malicious connections. Business-critical devices were placed on separate VLANs with tight traffic restrictions. Inside the network, security was sometimes enhanced by host-based firewalls, encryption, and identity management systems.
As new technologies entered the market and the network perimeters started to become less clearly defined, it became apparent that traditional security solutions could not be easily adapted to protect against many security threats that targeted low-priority systems and then spread laterally using trusted network connections. Fast advancement of virtual and mixed networking environments exacerbated the problem with a growing security debt on many networks.
Reliance on security concepts inherited from physical networks (such as IPs, subnets, and VLANs) could not solve security concerns within virtual environments and created bottlenecks around physical firewalls in mixed networks. Perimeter-centric security designs were costly, rigid, and difficult to maintain. They lacked the granularity, visibility, and automation to make network security transparent, ubiquitous, persistent, and intelligent.
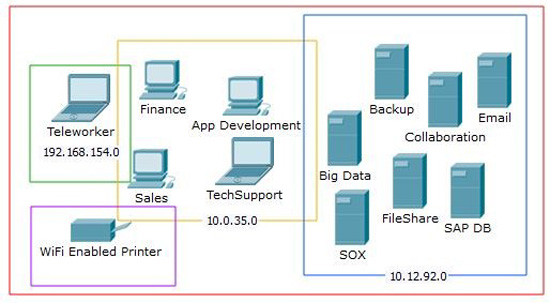
What is micro-segmentation?
Micro-segmentation is a cyber security technique that segments the network based on a diverse set of variables to describe various security zones. In addition to utilizing IPs and VLANs, micro-segmentation allows security zones (micro-segments) to be described using various host-centric attributes (such as OS, hardware, behavior) or application-driven attributes (such as where the workload is residing and how it is behaving) in order to improve visibility and security around those attributes and behaviors.
Game-changing aspects of micro-segmentation
The ability to logically segment networks based on the above attributes offers the security administrators significant flexibility in designing network access policies. Due to its independence from network boundaries, micro-segmentation techniques could be used to achieve better control over interactions among individual endpoints on any cross-platform network, on-premises or in the cloud.
Activity in various new network segments could be more easily tracked and analyzed. Security could now be strategically designed around specific endpoints and workloads. Hosts exhibiting suspicious behaviors could be more easily monitored or isolated. Hosts’ access control policies can be made more adaptive to changing network environments, agile, discriminating, and strategic.
As networks continue to become more diverse, dynamic, borderless, and virtualized, the old security architecture is no longer adequate. Micro-segmentation gives network security specialists new building blocks from which they can design more agile and affordable security solutions to better defend against ever-evolving security threats.