TLS-SSL Security Assurance
ESP Case study: TLS/SSL (Transport Layer) security assurance and audit preparation
The Problem
The migration from SSL /Early TLS to TLS 1.2 and 1.3 is currently underway. The PCI Security Standards Council made the requirement for the migration official in PCI DSS v3.2.1. Microsoft announced the end of support for TLS1.0 and 1.1 in Office 365 as of October 31, 2018. Services like DigiCert, ZenDesk, and Salesforce have pulled support for those protocols during 2018, as well. Chrome, Edge, IE, Firefox, and Safari announced that early TLS versions would not be supported by 2020.
However, migration issues are forcing the companies to take a cautious approach to the adoption of the new standard. Some standard Windows protocols, like RDP, do not easily support TLS 1.2 and higher. Patches for some system components, like MS SQL, have produced mixed results. As a result, the migration process has not been painless for the organizations.
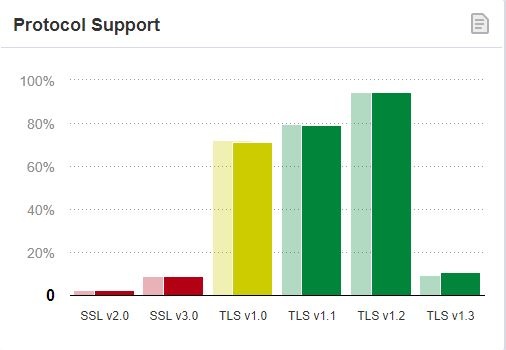
According to SSLabs, among the websites that they scan, thousands still support TLS 1.1 and below.
Automated TLS Security Policy: Express - Monitor - Enforce
For many organizations, setting complex security and compliance policies (like TLS hardening) is a continuous effort that requires a tremendous amount of manual work, inventorying, scripting, querying and debugging. Monitoring and enforcement are done haphazardly, often during audit preparation or during policy review.
Because ESP provides process automation at every step of policy lifecycle, organizations can now transition from a manual to an automatic policy management model: Express, Monitor, Enforce.

If you are one of the companies still struggling to find the right approach to complete the transition into newer TLS standards, ESP is the only tool on the market that:
- • enables easy maintenance of multiple TLS policies within the network to accommodate different functionality requirements
- • automates management and enforcement of TLS policies
- • allows instant tracking of TLS policies implementation and outcomes
- • generates detailed audit-ready lists of security controls and their exceptions
- • uses successful implementation of TLS controls in the calculation of cybersecurity risk scores
- • all from one unified easy-to-use web-based user interface.
How does ESP do it?
Express your TLS policy
First things first. Identify which machines in your environment require any type of special considerations when implementing TLS hardening policies, and then use ESP to easily separate them into different groups. You can then use ESP to tailor one or more TLS security policies to create policies tailored to those groups.
Define groups of machines for implementation of TLS hardening
- • Use ESP dynamic grouping feature to identify and select machines that require TLS hardening based on their roles or running applications
- • Define multiple groups of machines to be targeted for different TLS policies, if necessary
Next, use ESP to enable or disable proper controls to the appropriate groups of machines
Define and deploy encryption controls with ease using drag-and-drop ESP policy templates
- • Use ESP TLS policy template to create your own encryption hardening policies in minutes
- • Automatically disable or enable protocols and cipher suites at the registry level based on machine's group membership
- • Automatically disable or enable key exchange algorithms and hashing algorithms at the registry level
- • Create and modify entries in SCHANNEL remotely on all managed machines
Create compensating controls for applications that do not support new TLS versions
- • Create, deploy and document compensating controls (for example, micro-segmentation, registry-level control of weak ciphers, removal of downgrade functionality, etc) for those devices that require older versions of TLS or SSL to support proper functionality
- • Document your rationale for using compensating controls within the policy using Audit Notes annotations
Monitor your TLS policy
With ESP, your organization can begin continuous monitoring of the implementation and outcomes of your TLS policies as soon as they are deployed. If needed, EPS also generates detailed audit-ready lists of all deployed security controls and their exceptions. If your organization tracks risk, the risk scores of the compliant or non-compliant machines are updated and displayed automatically.
Automatically identify and monitor "out of compliance" devices
- • Have an at-a-glance view of all TLS policy-compliant and non-compliant devices
- • Use ESP dynamic grouping feature to automatically group non-compliance machines together for easier monitoring
- • Effortlessly monitor traffic and port activity on non-compliant machines
Use TLS policy compliance information to calculate risk and compliance levels
- • Use unbiased information collected directly from managed devices to immediately reflect on your PCI compliance levels
- • Use ESP Risk Management capabilities to automatically assign quantitative risk scores to in-compliance and out-of-compliance devices
Generate policy implementation reports and audit-ready implementation information
- • Generate detailed reports demonstrating policy implementation statistics and implementation gaps
- • Demonstrate historic policy compliance and enforcement trends
- • Automatically generate audit-ready, time-stamped documentation detailing changes to encryption policy composition or deployment to all affected devices
Enforce your TLS policy
Take proactive measures to make sure that organizational or environmental changes on the network do not impact your PCI compliance or your network security. Use automation to maintain and enforce uniform compliance with your policies across the network.
Enforce compliance with encryption-related policies across the network
- • Detect changes in monitored encryption settings and automatically generate detailed support tickets
- • Automatically enforce compliance with encryption policies, if needed
- • Use ESP micro-segmentation process to modify their network access rights to certain resources on the network
For many organizations, migration from the early TLS protocols is a challenging task that requires careful planning and implementation. Automation tools like ESP can provide for better flexibility in the process of implementation of the new requirements by allowing the creation of multiple TLS policies, automated monitoring of implementation outcomes, enforcement of TLS policies, and automated generation of audit trail documents. In the process, ESP can help you to reduce the workload on the IT team, improve visibility into the risk profile of the network, and reduce the likelihood of security breach due to SSL/TLS vulnerabilities.
Click here to request more information or an online demo
